7. 网络连接¶
RV06板卡有多种网络连接方式,包括有线网口连接、wifi连接、USB RNDIS连接。下面分别介绍这三种连接方式。
7.1. 网口连接¶
RV06板卡板载100M有线网口,支持10/100M自适应,支持全双工/半双工自适应,
当网口未插入时,网口的黄灯和绿灯都是熄灭的状态
当系统识别到网口插入时,黄灯会随网络状态闪烁,绿灯会常亮
插入网口后系统会自动获取ip地址,可以通过以下命令查看ip地址
1 | ifconfig
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | # ifconfig
eth0 Link encap:Ethernet HWaddr 2A:62:33:CC:9A:A8
inet addr:192.168.103.157 Bcast:192.168.103.255 Mask:255.255.255.0
inet6 addr: fe80::b152:83fe:59ae:c697/64 Scope:Link
inet6 addr: fd0f:2820:2b7b:0:1527:e688:1a45:1e91/64 Scope:Global
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:562 errors:0 dropped:0 overruns:0 frame:0
TX packets:120 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:51590 (50.3 KiB) TX bytes:11306 (11.0 KiB)
Interrupt:55
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:118 errors:0 dropped:0 overruns:0 frame:0
TX packets:118 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:8910 (8.7 KiB) TX bytes:8910 (8.7 KiB)
|
7.2. USB RNDIS连接¶
RNDIS使用的是固定IP地址: 192.168.137.100
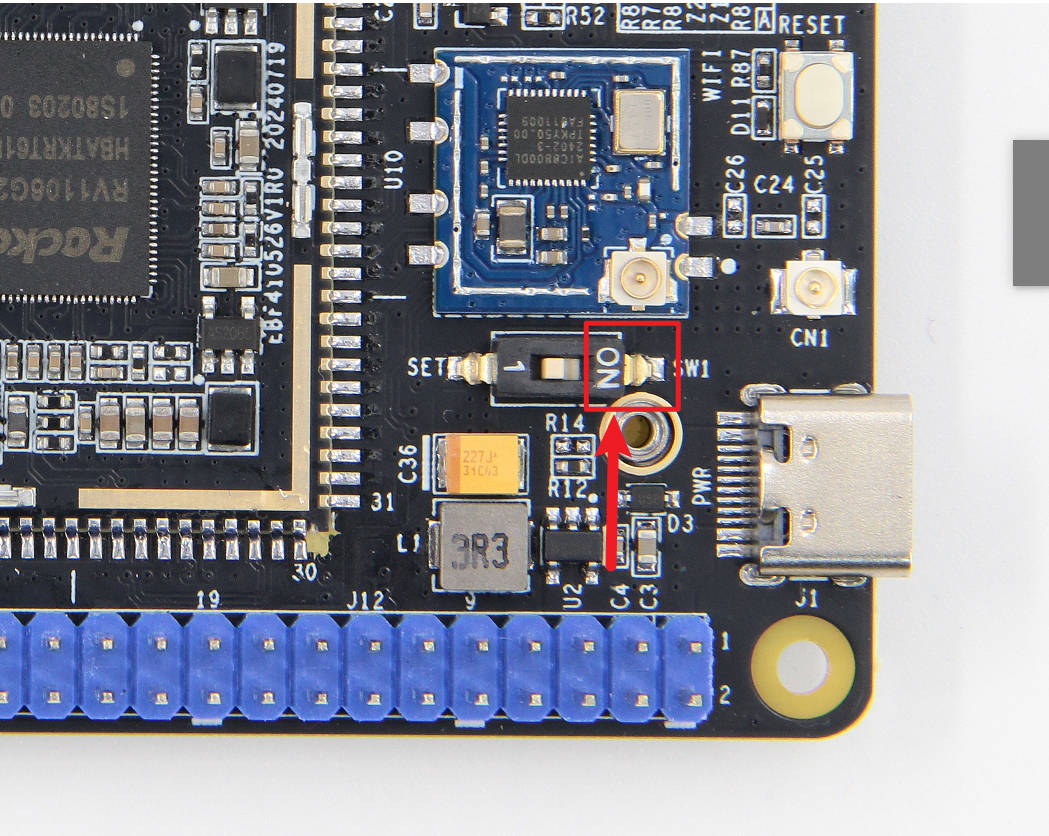
RV06板卡的type-c口是otg接口,可以将该接口设置成
device模式由于RV1106 芯片上只有一个USB2.0的接口,切换使用type-c接口时,需要将type-c接口的usb开启,即需要将板载的拨码开关拨到
ON运行的时候需要使用usb线连接电脑和板卡上。
配置文件
/etc/usb_config,将OTG_MODE设置为peripheral
1 2 3 4 5 6 7 8 | # cat /etc/usb_config
# OTG_MODE:host or peripheral
# OTG_MODE=peripheral
OTG_MODE=host
# GADGET_CONFIG:usb_mtp_en usb_ums_en usb_ntb_en
# usb_acm_en usb_uac1_en usb_uac2_en usb_uvc_en usb_rndis_en usb_hid_en
GADGET_CONFIG="usb_rndis_en"
|
将上述文件配置改成下面配置
1 2 3 4 5 6 7 8 | # cat /etc/usb_config
# OTG_MODE:host or peripheral
OTG_MODE=peripheral
# OTG_MODE=host
# GADGET_CONFIG:usb_mtp_en usb_ums_en usb_ntb_en
# usb_acm_en usb_uac1_en usb_uac2_en usb_uvc_en usb_rndis_en usb_hid_en
GADGET_CONFIG="usb_rndis_en"
|
重启或者执行下面命令生效
1 2 3 | reboot
# 或
/etc/init.d/S50usbdevice start
|
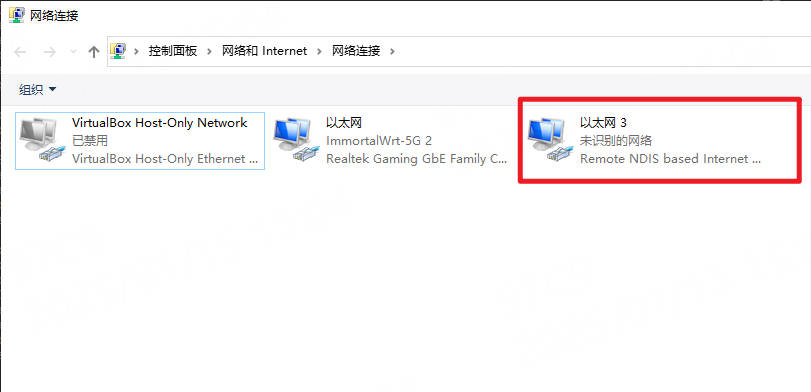
RNDIS在Windows系统上是免驱的,所以可以看到 更改适配器选项 中的 网络连接 里会多了下面的设置
7.2.1. 共享网络¶
如果想让板卡连接上网络,可以启动网络共享
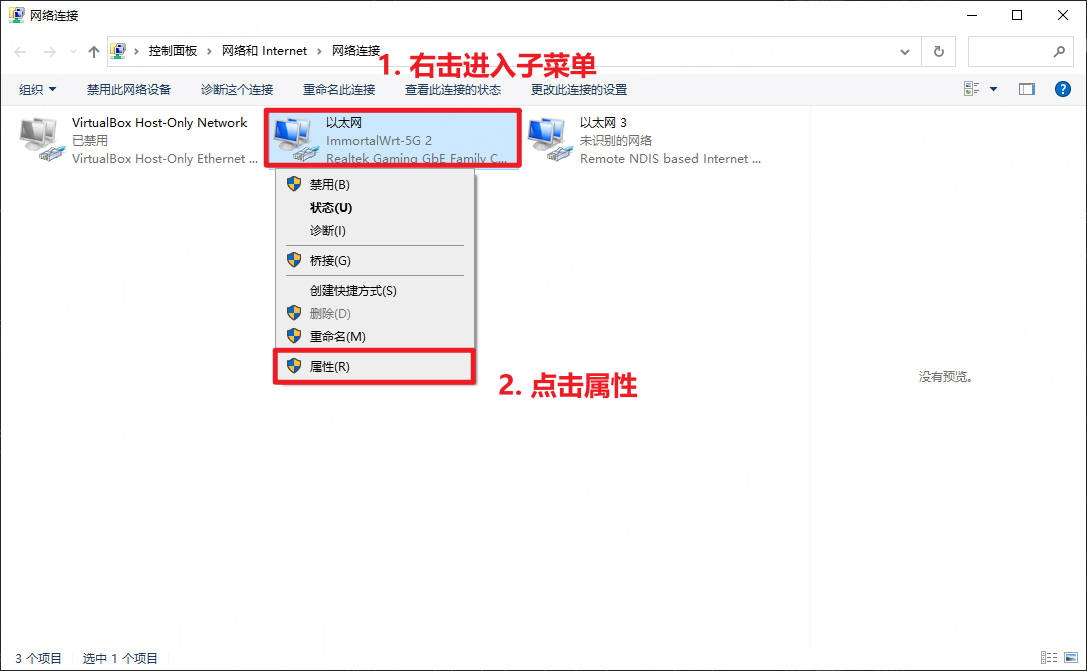
进入
更改适配器选项中的网络连接右击有网络的连接,点击
属性
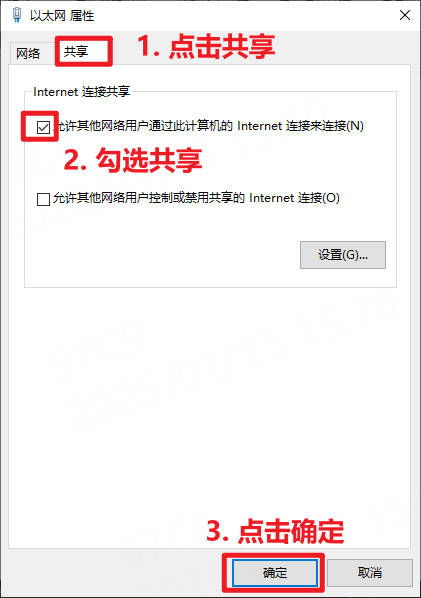
然后点击
共享,勾选允许其他网络用户通过此计算机的Internet连接来连接,点击确定
然后可以看到网络上写着
共享的
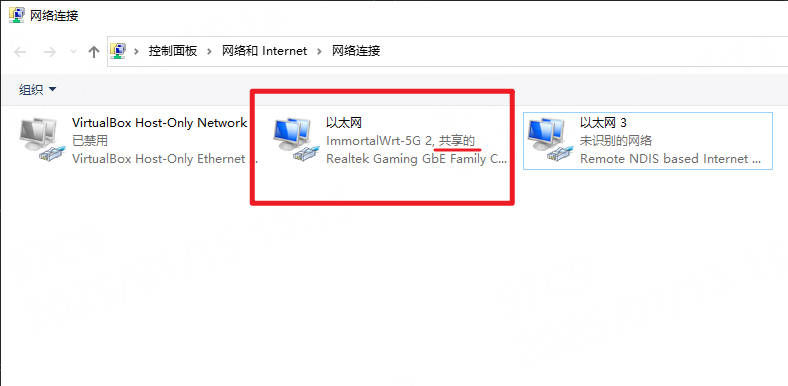
这时候板卡就可以连接到电脑上,使用电脑的网络进行上网了。
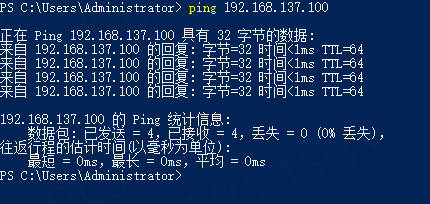
可以使用在power shell上使用ping查看网络连接情况
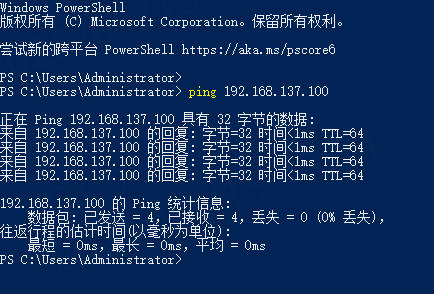
7.2.2. 手动设置¶
如果不想让板子运行在有网络的环境
进入
更改适配器选项中的网络连接右击rndis的连接,点击
属性
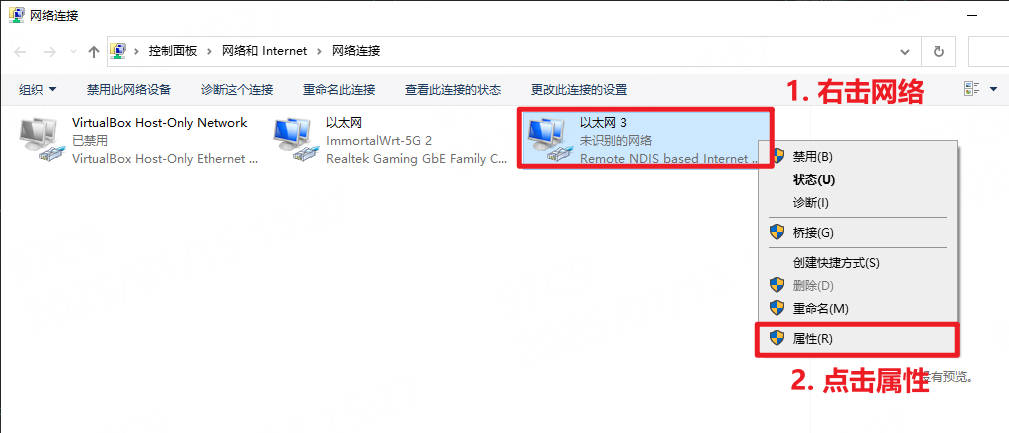
双击
Internet协议版本4(TCP/IPv4)
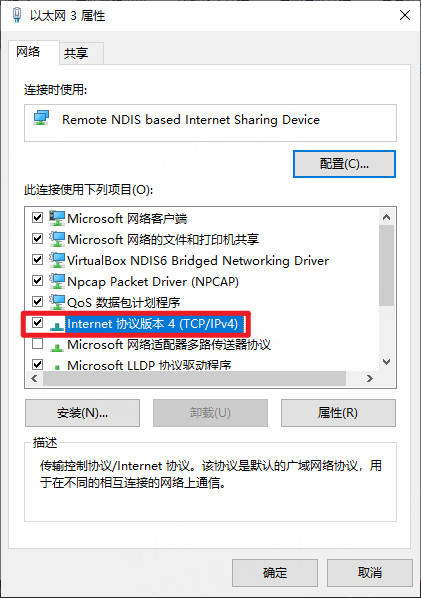
进入配置,按下图配置
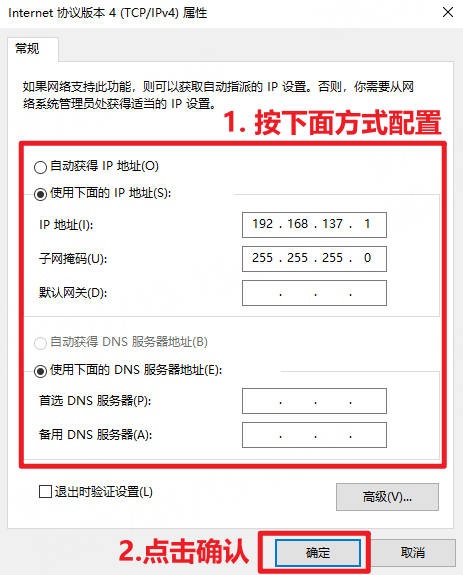
最后点击确定,这时候板卡就可以连接到电脑上。
7.2.3. 取消rndis连接¶
配置文件
/etc/usb_config,将OTG_MODE设置为host
1 2 3 4 5 6 7 8 | # cat /etc/usb_config
# OTG_MODE:host or peripheral
OTG_MODE=peripheral
# OTG_MODE=host
# GADGET_CONFIG:usb_mtp_en usb_ums_en usb_ntb_en
# usb_acm_en usb_uac1_en usb_uac2_en usb_uvc_en usb_rndis_en usb_hid_en
GADGET_CONFIG="usb_rndis_en"
|
将上述文件配置改成下面配置
1 2 3 4 5 6 7 8 | # cat /etc/usb_config
# OTG_MODE:host or peripheral
# OTG_MODE=peripheral
OTG_MODE=host
# GADGET_CONFIG:usb_mtp_en usb_ums_en usb_ntb_en
# usb_acm_en usb_uac1_en usb_uac2_en usb_uvc_en usb_rndis_en usb_hid_en
GADGET_CONFIG="usb_rndis_en"
|
重启或者执行下面命令生效
1 2 3 | reboot
# 或
/etc/init.d/S50usbdevice stop
|
7.3. wifi连接¶
RV06板卡板载USB接口的2.4GHz单频WIFI6模块
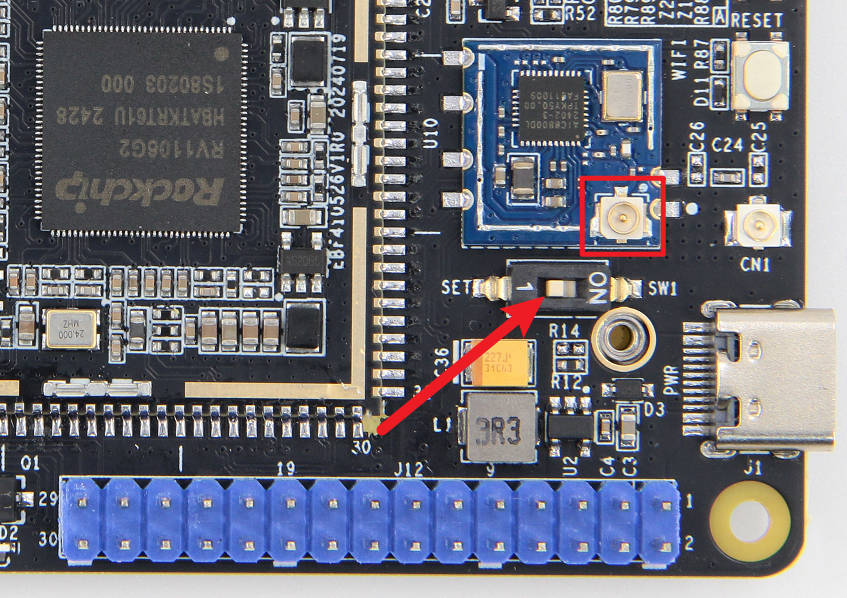
AIC8800DL由于RV1106 芯片上只有一个USB2.0的接口,切换使用WIFI时,需要将type-c接口的usb关闭切换到wifi上,需要将板载的拨码开关拨到
1RV06板卡连接WIFI需要连接WiFi天线,天线接口是
ipx-1类型,需要注意的是,天线需要接到板载模块上面,连接板上的天线接口不会有信号,如下图所示
7.3.1. 配置文件配置wifi¶
RV06使用 wpa_supplicant 工具进行wifi连接,连接wifi前需要先配置wifi的ssid和密码,配置文件路径为 /etc/wpa_supplicant.conf
1 2 3 4 5 6 7 8 9 | # cat /etc/wpa_supplicant.conf
ctrl_interface=/var/run/wpa_supplicant
update_config=1
network={
ssid="aEBF_Guest"
psk="BQTH4kH9"
key_mgmt=WPA-PSK
}
|
配置文件中ssid和psk为需要连接的wifi的名称和密码,key_mgmt为加密方式,WPA-PSK为WIFI密码加密方式
配置文件中可以配置多个wifi,系统会自动选择信号最好的wifi进行连接
7.3.2. wpa_cli连接wifi¶
使用
wpa_cli工具连接wifi,命令行输入下面命令,进入配置
1 | wpa_cli
|
1 2 3 4 5 6 7 8 9 10 11 12 13 | # wpa_cli
wpa_cli v2.10
Copyright (c) 2004-2022, Jouni Malinen <j@w1.fi> and contributors
This software may be distributed under the terms of the BSD license.
See README for more details.
Selected interface 'wlan0'
Interactive mode
>
|
输入命令后可以看到进入了新的命令行,输入
help可以查看wpa_cli的命令帮助
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 | > help
commands:
status [verbose] = get current WPA/EAPOL/EAP status
ifname = get current interface name
ping = pings wpa_supplicant
relog = re-open log-file (allow rolling logs)
note <text> = add a note to wpa_supplicant debug log
mib = get MIB variables (dot1x, dot11)
help [command] = show usage help
interface [ifname] = show interfaces/select interface
level <debug level> = change debug level
license = show full wpa_cli license
quit = exit wpa_cli
set = set variables (shows list of variables when run without arguments)
dump = dump config variables
get <name> = get information
driver_flags = list driver flags
logon = IEEE 802.1X EAPOL state machine logon
logoff = IEEE 802.1X EAPOL state machine logoff
pmksa = show PMKSA cache
pmksa_flush = flush PMKSA cache entries
reassociate = force reassociation
reattach = force reassociation back to the same BSS
preauthenticate <BSSID> = force preauthentication
identity <network id> <identity> = configure identity for an SSID
password <network id> <password> = configure password for an SSID
new_password <network id> <password> = change password for an SSID
pin <network id> <pin> = configure pin for an SSID
otp <network id> <password> = configure one-time-password for an SSID
psk_passphrase <network id> <PSK/passphrase> = configure PSK/passphrase for an SSID
passphrase <network id> <passphrase> = configure private key passphrase
for an SSID
sim <network id> <pin> = report SIM operation result
bssid <network id> <BSSID> = set preferred BSSID for an SSID
bssid_ignore <BSSID> = add a BSSID to the list of temporarily ignored BSSs
bssid_ignore clear = clear the list of temporarily ignored BSSIDs
bssid_ignore = display the list of temporarily ignored BSSIDs
blacklist = deprecated alias for bssid_ignore
log_level <level> [<timestamp>] = update the log level/timestamp
log_level = display the current log level and log options
list_networks = list configured networks
select_network <network id> = select a network (disable others)
enable_network <network id> = enable a network
disable_network <network id> = disable a network
add_network = add a network
remove_network <network id> = remove a network
set_network <network id> <variable> <value> = set network variables (shows
list of variables when run without arguments)
get_network <network id> <variable> = get network variables
dup_network <src network id> <dst network id> <variable> = duplicate network variables
list_creds = list configured credentials
add_cred = add a credential
remove_cred <cred id> = remove a credential
set_cred <cred id> <variable> <value> = set credential variables
get_cred <cred id> <variable> = get credential variables
save_config = save the current configuration
disconnect = disconnect and wait for reassociate/reconnect command before
connecting
reconnect = like reassociate, but only takes effect if already disconnected
scan = request new BSS scan
scan_results = get latest scan results
abort_scan = request ongoing scan to be aborted
bss <<idx> | <bssid>> = get detailed scan result info
get_capability <eap/pairwise/group/key_mgmt/proto/auth_alg/channels/freq/modes> = get capabilities
reconfigure = force wpa_supplicant to re-read its configuration file
terminate = terminate wpa_supplicant
interface_add <ifname> <confname> <driver> <ctrl_interface> <driver_param>
<bridge_name> <create> <type> = adds new interface, all parameters but
<ifname> are optional. Supported types are station ('sta') and AP ('ap')
interface_remove <ifname> = removes the interface
interface_list = list available interfaces
ap_scan <value> = set ap_scan parameter
scan_interval <value> = set scan_interval parameter (in seconds)
bss_expire_age <value> = set BSS expiration age parameter
bss_expire_count <value> = set BSS expiration scan count parameter
bss_flush <value> = set BSS flush age (0 by default)
ft_ds <addr> = request over-the-DS FT with <addr>
wps_pbc [BSSID] = start Wi-Fi Protected Setup: Push Button Configuration
wps_pin <BSSID> [PIN] = start WPS PIN method (returns PIN, if not hardcoded)
wps_check_pin <PIN> = verify PIN checksum
wps_cancel Cancels the pending WPS operation
wps_reg <BSSID> <AP PIN> = start WPS Registrar to configure an AP
wps_ap_pin [params..] = enable/disable AP PIN
wps_er_start [IP address] = start Wi-Fi Protected Setup External Registrar
wps_er_stop = stop Wi-Fi Protected Setup External Registrar
wps_er_pin <UUID> <PIN> = add an Enrollee PIN to External Registrar
wps_er_pbc <UUID> = accept an Enrollee PBC using External Registrar
wps_er_learn <UUID> <PIN> = learn AP configuration
wps_er_set_config <UUID> <network id> = set AP configuration for enrolling
wps_er_config <UUID> <PIN> <SSID> <auth> <encr> <key> = configure AP
ibss_rsn <addr> = request RSN authentication with <addr> in IBSS
suspend = notification of suspend/hibernate
resume = notification of resume/thaw
roam <addr> = roam to the specified BSS
vendor_elem_add <frame id> <hexdump of elem(s)> = add vendor specific IEs to frame(s)
0: Probe Req (P2P), 1: Probe Resp (P2P) , 2: Probe Resp (GO), 3: Beacon (GO), 4: PD Req, 5: PD Resp, 6: GO Neg Req, 7: GO Neg Resp, 8: GO Neg Conf, 9: Inv Req, 10: Inv Resp, 11: Assoc Req (P2P), 12: Assoc Resp (P2P)
vendor_elem_get <frame id> = get vendor specific IE(s) to frame(s)
0: Probe Req (P2P), 1: Probe Resp (P2P) , 2: Probe Resp (GO), 3: Beacon (GO), 4: PD Req, 5: PD Resp, 6: GO Neg Req, 7: GO Neg Resp, 8: GO Neg Conf, 9: Inv Req, 10: Inv Resp, 11: Assoc Req (P2P), 12: Assoc Resp (P2P)
vendor_elem_remove <frame id> <hexdump of elem(s)> = remove vendor specific IE(s) in frame(s)
0: Probe Req (P2P), 1: Probe Resp (P2P) , 2: Probe Resp (GO), 3: Beacon (GO), 4: PD Req, 5: PD Resp, 6: GO Neg Req, 7: GO Neg Resp, 8: GO Neg Conf, 9: Inv Req, 10: Inv Resp, 11: Assoc Req (P2P), 12: Assoc Resp (P2P)
sta_autoconnect <0/1> = disable/enable automatic reconnection
tdls_discover <addr> = request TDLS discovery with <addr>
tdls_setup <addr> = request TDLS setup with <addr>
tdls_teardown <addr> = tear down TDLS with <addr>
tdls_link_status <addr> = TDLS link status with <addr>
wmm_ac_addts <uplink/downlink/bidi> <tsid=0..7> <up=0..7> [nominal_msdu_size=#] [mean_data_rate=#] [min_phy_rate=#] [sba=#] [fixed_nominal_msdu] = add WMM-AC traffic stream
wmm_ac_delts <tsid> = delete WMM-AC traffic stream
wmm_ac_status = show status for Wireless Multi-Media Admission-Control
tdls_chan_switch <addr> <oper class> <freq> [sec_channel_offset=] [center_freq1=] [center_freq2=] [bandwidth=] [ht|vht] = enable channel switching with TDLS peer
tdls_cancel_chan_switch <addr> = disable channel switching with TDLS peer <addr>
signal_poll = get signal parameters
signal_monitor = set signal monitor parameters
pktcnt_poll = get TX/RX packet counters
reauthenticate = trigger IEEE 802.1X/EAPOL reauthentication
raw <params..> = Sent unprocessed command
flush = flush wpa_supplicant state
radio_work = radio_work <show/add/done>
vendor <vendor id> <command id> [<hex formatted command argument>] = Send vendor command
neighbor_rep_request [ssid=<SSID>] [lci] [civic] = Trigger request to AP for neighboring AP report (with optional given SSID in hex or enclosed in double quotes, default: current SSID; with optional LCI and location civic request)
twt_setup [dialog=<token>] [exponent=<exponent>] [mantissa=<mantissa>] [min_twt=<Min TWT>] [setup_cmd=<setup-cmd>] [twt=<u64>] [requestor=0|1] [trigger=0|1] [implicit=0|1] [flow_type=0|1] [flow_id=<3-bit-id>] [protection=0|1] [twt_channel=<twt chanel id>] [control=<control-u8>] = Send TWT Setup frame
twt_teardown [flags=<value>] = Send TWT Teardown frame
erp_flush = flush ERP keys
mac_rand_scan <scan|sched|pno|all> enable=<0/1> [addr=mac-address mask=mac-address-mask] = scan MAC randomization
get_pref_freq_list <interface type> = retrieve preferred freq list for the specified interface type
p2p_lo_start <freq> <period> <interval> <count> = start P2P listen offload
p2p_lo_stop = stop P2P listen offload
dpp_qr_code report a scanned DPP URI from a QR Code
dpp_bootstrap_gen type=<qrcode> [chan=..] [mac=..] [info=..] [curve=..] [key=..] = generate DPP bootstrap information
dpp_bootstrap_remove *|<id> = remove DPP bootstrap information
dpp_bootstrap_get_uri <id> = get DPP bootstrap URI
dpp_bootstrap_info <id> = show DPP bootstrap information
dpp_bootstrap_set <id> [conf=..] [ssid=<SSID>] [ssid_charset=#] [psk=<PSK>] [pass=<passphrase>] [configurator=<id>] [conn_status=#] [akm_use_selector=<0|1>] [group_id=..] [expiry=#] [csrattrs=..] = set DPP configurator parameters
dpp_auth_init peer=<id> [own=<id>] = initiate DPP bootstrapping
dpp_listen <freq in MHz> = start DPP listen
dpp_stop_listen = stop DPP listen
dpp_configurator_add [curve=..] [key=..] = add DPP configurator
dpp_configurator_remove *|<id> = remove DPP configurator
dpp_configurator_get_key <id> = Get DPP configurator's private key
dpp_configurator_sign conf=<role> configurator=<id> = generate self DPP configuration
dpp_pkex_add add PKEX code
dpp_pkex_remove *|<id> = remove DPP pkex information
dpp_controller_start [tcp_port=<port>] [role=..] = start DPP controller
dpp_controller_stop = stop DPP controller
dpp_chirp own=<BI ID> iter=<count> = start DPP chirp
dpp_stop_chirp = stop DPP chirp
all_bss = list all BSS entries (scan results)
mscs <add|remove|change> [up_bitmap=<hex byte>] [up_limit=<integer>] [stream_timeout=<in TUs>] [frame_classifier=<hex bytes>] = Configure MSCS request
scs [scs_id=<decimal number>] <add|remove|change> [scs_up=<0-7>] [classifier_type=<4|10>] [classifier params based on classifier type] [tclas_processing=<0|1>] [scs_id=<decimal number>] ... = Send SCS request
dscp_resp <[reset]>/<[solicited] [policy_id=1 status=0...]> [more] = Send DSCP response
dscp_query wildcard/domain_name=<string> = Send DSCP Query
>
|
可以看到命令会比较多,这里我们只介绍一些常用的命令
命令 |
命令说明 |
举例 |
|---|---|---|
status |
获取当前wifi连接状态 |
status |
scan |
搜索wifi |
scan |
scan_results |
搜到到的全部wifi名称等信息 |
scan_results |
set_network |
设置wifi的SSID和psk |
set_network 1 ssid “PPP” |
list_network |
列出所有的配置文件中的信息 |
list_network |
add_network |
添加一个网络 |
add_network |
disale_network |
禁止WiFi |
disale_network 1 |
select_network |
选择一个网络 |
select_network 1 |
remove_network |
根据网络ID删除 删除一个网络ID,根据网络ID删除 |
remove_network 1 |
quit |
退出wpa_cli |
quit |
disconnect |
断开连接 |
disconnect |
reconnect |
重新连接 |
reconnect |
下面将通过一个例子来演示如何使用wpa_cli命令来连接wifi
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 | # wpa_cli
wpa_cli v2.10
Copyright (c) 2004-2022, Jouni Malinen <j@w1.fi> and contributors
This software may be distributed under the terms of the BSD license.
See README for more details.
Selected interface 'wlan0'
Interactive mode
> status
bssid=34:f7:16:dc:b7:5c
freq=2462
ssid=aEBF_Guest
id=1
mode=station
wifi_generation=4
pairwise_cipher=CCMP
group_cipher=CCMP
key_mgmt=WPA2-PSK
wpa_state=COMPLETED
ip_address=10.169.169.7
address=38:7a:cc:65:78:20
uuid=45fde3ec-a3a3-53d8-9046-2f6af7bd32e0
ieee80211ac=1
>
> list_network
network id / ssid / bssid / flags
0 aEBF_Guest any [CURRENT]
>
> disconnect
OK
<3>CTRL-EVENT-DISCONNECTED bssid=34:f7:16:dc:b7:5c reason=3 locally_generated=1
<3>CTRL-EVENT-DSCP-POLICY clear_all
<3>CTRL-EVENT-REGDOM-CHANGE init=CORE type=WORLD
>
> remove_network 0
OK
<3>CTRL-EVENT-NETWORK-REMOVED 0
>
> list_networks
network id / ssid / bssid / flags
>
> scan
OK
<3>CTRL-EVENT-SCAN-STARTED
<3>CTRL-EVENT-SCAN-RESULTS
>
> scan_results
bssid / frequency / signal level / flags / ssid
fc:a0:5a:06:74:64 2447 -29 [WPA-PSK-CCMP+TKIP][WPA2-PSK-CCMP+TKIP][ESS] oraybox-2.4G
48:88:99:c9:16:82 2432 -33 [WPA2-PSK+SAE-CCMP-256+GCMP-256+CCMP+GCMP][ESS] TOTO_M0
34:fc:a1:73:4c:2b 2422 -62 [WPA-PSK-CCMP+TKIP][WPA2-PSK-CCMP+TKIP][WPS][ESS] 228
82:ea:07:e3:f3:81 2462 -61 [WPA-PSK-CCMP][WPA2-PSK-CCMP][ESS]
00:4b:f3:97:0c:6f 2472 -64 [WPA-PSK-CCMP][WPA2-PSK-CCMP][ESS] MERCURY_0C6F
34:f7:16:dc:b7:5c 2462 -20 [WPA-PSK-CCMP][WPA2-PSK-CCMP][ESS] aEBF_Guest
34:f7:16:dc:bd:a7 2452 -49 [WPA-PSK-CCMP][WPA2-PSK-CCMP][ESS] aEBF_Guest
42:c8:09:5d:2e:79 2412 -58 [WPA-PSK-CCMP+TKIP][WPA2-PSK-CCMP+TKIP][WPS][ESS] 228-5G
36:f7:16:1c:b7:5c 2462 -21 [ESS] aEBF_Office
36:f7:16:1c:bd:a7 2452 -50 [ESS] aEBF_Office
36:f7:16:1c:bd:83 2462 -59 [ESS] aEBF_Office
>
> add_network
0
<3>CTRL-EVENT-NETWORK-ADDED 0
>
> set_network 0 ssid "TOTO_M0"
OK
>
> set_network 0 key_mgmt WPA-PSK
OK
>
> set_network 0 psk "pass123456789"
OK
>
> enable_network 0
OK
>
> save_config
OK
>
> list_networks
network id / ssid / bssid / flags
0 TOTO_M0 any
>
> select_network 0
OK
<3>CTRL-EVENT-SCAN-STARTED
<3>CTRL-EVENT-SCAN-RESULTS
<3>WPS-AP-AVAILABLE
<3>Trying to associate with 48:88:99:c9:16:82 (SSID='TOTO_M0' freq=2432 MHz)
<3>Associated with 48:88:99:c9:16:82
<3>CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
<3>WPA: Key negotiation completed with 48:88:99:c9:16:82 [PTK=CCMP GTK=CCMP]
<3>CTRL-EVENT-CONNECTED - Connection to 48:88:99:c9:16:82 completed [id=1 id_str=]
>
> status
bssid=48:88:99:c9:16:82
freq=2432
ssid=TOTO_M0
id=0
mode=station
wifi_generation=6
pairwise_cipher=CCMP
group_cipher=CCMP
key_mgmt=WPA2-PSK
wpa_state=COMPLETED
ip_address=192.168.103.139
address=38:7a:cc:65:78:20
uuid=45fde3ec-a3a3-53d8-9046-2f6af7bd32e0
ieee80211ac=1
>
> quit
# ifconfig wlan0
wlan0 Link encap:Ethernet HWaddr 38:7A:CC:65:78:20
inet addr:192.168.103.139 Bcast:192.168.103.255 Mask:255.255.255.0
inet6 addr: fdf5:49a3:57bb::ff5/128 Scope:Global
inet6 addr: fdf5:49a3:57bb:0:94c0:a9ae:3183:6cd9/64 Scope:Global
inet6 addr: fe80::3a7a:ccff:fe65:7820/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:39595 errors:0 dropped:5 overruns:0 frame:0
TX packets:192662 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2619579 (2.4 MiB) TX bytes:288643449 (275.2 MiB)
# ping baidu.com
PING baidu.com (39.156.66.10): 56 data bytes
64 bytes from 39.156.66.10: seq=0 ttl=47 time=43.113 ms
64 bytes from 39.156.66.10: seq=1 ttl=47 time=42.159 ms
64 bytes from 39.156.66.10: seq=2 ttl=47 time=57.048 ms
64 bytes from 39.156.66.10: seq=3 ttl=47 time=42.163 ms
# cat /etc/wpa_supplicant.conf
ctrl_interface=/var/run/wpa_supplicant
update_config=1
network={
ssid="TOTO_M0"
psk="pass123456789"
key_mgmt=WPA-PSK
}
cat
|
status: 可以看到刚开始的时候板卡连接了aEBF_Guest这个WIFI, IP地址是10.169.169.7list_network: 可以看到当前连接的WiFi是aEBF_Guest,编号为0disconnect: 断开aEBF_GuestWIFI的连接remove_network 0: 删除编号为0的WIFI,也就是aEBF_Guest这个WIFIlist_networks: 可以看到WIFI列表为空scan: 扫描附近的WIFIscan_results: 可以看到扫描到了很多的WIFI,后面以TOTO_M0这个WIFI连接为例add_network:添加一个WIFI网络,获得编号为0set_network 0 ssid "TOTO_M0": 设置编号为0的WIFI的ssid为TOTO_M0set_network 0 key_mgmt WPA-PSK: 设置编号为0的WIFI的加密方式为WPA-PSKset_network 0 psk "pass123456789": 设置编号为0的WIFI的密码为pass123456789enable_network 0: 启用编号为0的WIFIsave_config: 保存配置list_networks: 可以看到WIFI列表中多了一个编号为0的WIFI,SSID为TOTO_M0select_network 0: 连接编号为0的WIFI,可以看到连接成功了status: 可以看到当前连接的WiFi是TOTO_M0,并且IP地址是 192.168.103.139quit: 退出程序ifconfig wlan0: 可以看到wlan0网卡的信息,包括IP地址,MAC地址等ping baidu.com: 可以看到ping百度服务器的结果cat /etc/wpa_supplicant.conf: 可以看到wpa_supplicant的配置文件,包括连接的WiFi的SSID和密码等
整个过程还是比较复杂的,需要耐心操作。
